Don’t Fall for Fake
Don’t bite that phishing hook!
Let's talk
What is this phishing thing, anyway?
Phishing is when someone tries to steal information like your login or account details by pretending to be someone you trust in an email, text, or other online communication. Phishing emails – and the unsafe sites they try to send you to or the attachments they try to get you to open – can also put viruses on your computer. Some viruses use your contacts list to target your friends and family with the same, or a more personalized, phishing attack. Other types of scams might try to trick you into downloading malware or unwanted software by telling you that thereʼs something wrong with your device. Remember: A website or ad canʼt tell if thereʼs anything wrong with your machine!
Some phishing attacks are obviously fake. Others can be sneaky and really convincing – like when a scammer sends you a message that includes some of your personal information. Thatʼs called spearphishing, and it can be very difficult to spot because using your info can make it seem like they know you.
Before you click on a link or enter your password in a site you haven’t been to before, itʼs a good idea to ask yourself some questions about that email or webpage. Here are some questions you could ask:
- Does it look professional like other websites you know and trust, with the product’s or company’s usual logo and with text that is free of spelling errors?
- Does the siteʼs URL match the product’s or company’s name and information youʼre looking for? Are there misspellings?
- Are there any spammy pop-ups?
- Does the URL start with https://with a little green padlock to the left of it? (That means the connection is secure.)
- Whatʼs in the fine print? (Thatʼs often where they put sneaky stuff.)
- Is the email or site offering something that sounds too good to be true, like a chance to make a lot of money? (It’s almost always too good to be true.)
- Does the message sound just a little bit weird? Like they might know you, but you’re not completely sure?
And what if you do fall for a scam? Start with this: Donʼt panic!
- Tell your parent, teacher, or other trusted adult right away. The longer you wait, the worse things could get.
- Change your passwords for online accounts.
- If you do get tricked by a scam, let your friends and people in your contacts know right away, because they could be targeted next.
- Use settings to report the message as spam, if possible.
Activity
Study examples
Let’s make your children study these examples of messages and websites.
Indicate choices
Select “Real’ or “Fake” for each example, and say why below.
Discuss choices
Which examples appeared trustworthy and which seemed suspicious? Did any of the answers surprise you?
Further discussion
Here are some more questions to ask yourself when assessing messages and sites you find online:
Does this message look right?
What’s your first impression? Do any aspects strike you as being untrustworthy?
Is the email offering you something for free?
Free offers usually aren’t really free (even if there are).
Is the message asking for your personal information?
Some websites ask for personal info so they can send you more scams. For example, a “personality test” in which you disclose personal information that can be used to make it easy to guess your password or other secret information. Most genuine businesses will never ask for personal information by email.
Is it a chain email or post on social media?
Emails and posts that ask you to forward it to everyone you know can put you and others at risk. Don’t do it unless you’re sure of the source and sure the message is safe to pass on.
Read the fine print
At the bottom of most documents you’ll find the fine print. This text is tiny, and often contains the stuff they want you to miss. For example, a headline at the top might say you’ve won a free phone, but in the fine print you’ll read that you actually have to pay that company $200 per month.
Worksheet
Phishing examples
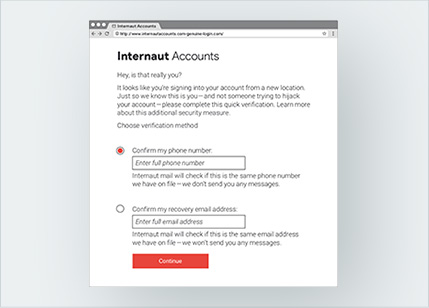
1. Is this real or fake?
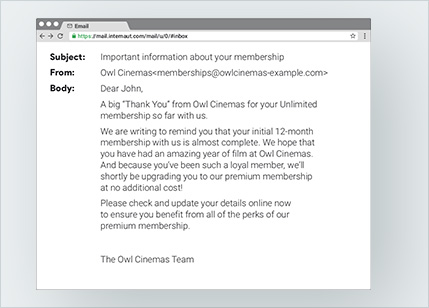
2. Is this real or fake?
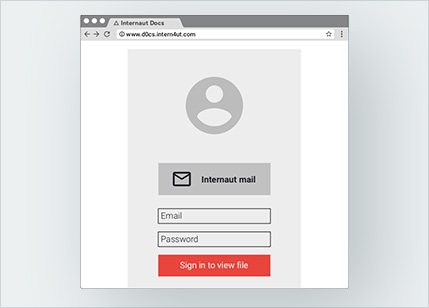
3. Is this real or fake?
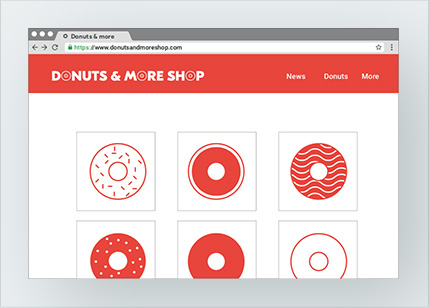
4. Is this real or fake?
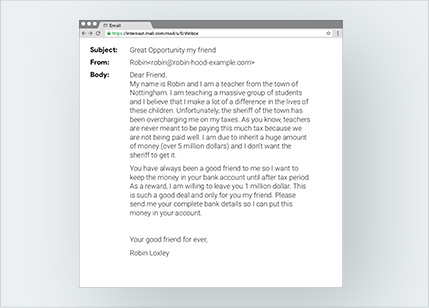
5. Is this real or fake?
Takeaway
When you’re online, always be on the lookout for phishing attacks in emails, texts, and posted messages—and make sure you tell the right people about it if you do get fooled.









 In the Play Store, go to Menu > Settings > Parental controls.
In the Play Store, go to Menu > Settings > Parental controls. To set this for the App Store, go to Settings > General > Limitations > Allowed Content on your iPhone or iPad.
To set this for the App Store, go to Settings > General > Limitations > Allowed Content on your iPhone or iPad.